第 5 章:流量控制 - 细粒度流量路由
本文梳理了 Istio 在流量路由、版本灰度、流量镜像及集群外流量管理等方面的核心能力,适合云原生环境下微服务治理的实践参考。
部署与发布的风险控制
在微服务环境中,部署新版本时需降低风险。Istio 支持蓝绿部署、金丝雀发布等模式,实现部署与发布解耦。通过先部署新版本但不分配流量,结合流量路由策略,逐步将流量引入新版本,便于监控和回滚。
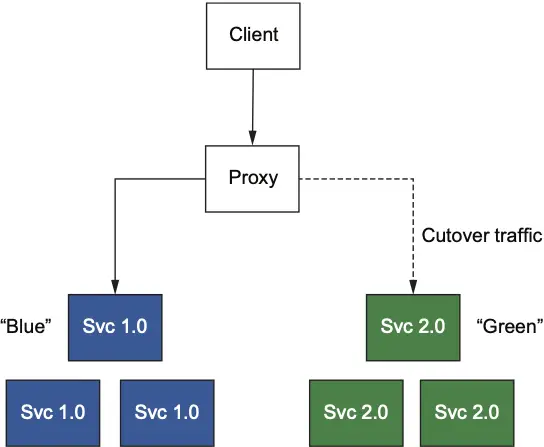
Istio 流量路由基础
Istio 通过 VirtualService 和 DestinationRule 实现细粒度流量路由。可基于请求头、权重等条件,将流量分配到不同版本,实现暗启动、金丝雀等策略。
环境准备与服务部署
- 切换命名空间并清理环境:
kubectl config set-context $(kubectl config current-context) --namespace=istioinaction
kubectl delete deployment,svc,gateway,virtualservice,destinationrule --all -n istioinaction
- 部署 catalog v1 服务:
kubectl apply -f services/catalog/kubernetes/catalog.yaml
- 创建 Gateway 和 VirtualService 公开服务:
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: catalog-gateway
spec:
selector:
istio: ingressgateway
servers:
- port: { number: 80, name: http, protocol: HTTP }
hosts: [ "catalog.istioinaction.io" ]
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: catalog-vs-from-gw
spec:
hosts: [ "catalog.istioinaction.io" ]
gateways: [ catalog-gateway ]
http:
- route:
- destination: { host: catalog }
- 访问服务:
curl http://localhost/items -H "Host: catalog.istioinaction.io"
多版本部署与流量分配
- 部署 catalog v2:
kubectl apply -f services/catalog/kubernetes/catalog-deployment-v2.yaml
- 定义 DestinationRule 区分版本:
apiVersion: networking.istio.io/v1alpha3
kind: DestinationRule
metadata:
name: catalog
spec:
host: catalog
subsets:
- name: version-v1
labels: { version: v1 }
- name: version-v2
labels: { version: v2 }
- 将所有流量路由到 v1:
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: catalog-vs-from-gw
spec:
hosts: [ "catalog.istioinaction.io" ]
gateways: [ catalog-gateway ]
http:
- route:
- destination: { host: catalog, subset: version-v1 }
- 基于请求头路由到 v2(暗启动):
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: catalog-vs-from-gw
spec:
hosts: [ "catalog.istioinaction.io" ]
gateways: [ catalog-gateway ]
http:
- match:
- headers:
x-istio-cohort:
exact: "internal"
route:
- destination: { host: catalog, subset: version-v2 }
- route:
- destination: { host: catalog, subset: version-v1 }
- 权重分流(金丝雀发布):
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: catalog
spec:
hosts: [ catalog ]
gateways: [ mesh ]
http:
- route:
- destination: { host: catalog, subset: version-v1 }
weight: 90
- destination: { host: catalog, subset: version-v2 }
weight: 10
流量迁移自动化
手动调整权重易出错,可借助 Flagger 工具自动化金丝雀发布。Flagger 结合 Prometheus 指标,自动推进流量迁移、健康检查与回滚。
- 安装 Flagger 并配置 Canary 资源:
apiVersion: flagger.app/v1beta1
kind: Canary
metadata:
name: catalog-release
namespace: istioinaction
spec:
targetRef:
apiVersion: apps/v1
kind: Deployment
name: catalog
service:
name: catalog
port: 80
targetPort: 3000
gateways: [ mesh ]
hosts: [ catalog ]
analysis:
interval: 45s
threshold: 5
maxWeight: 50
stepWeight: 10
metrics:
- name: request-success-rate
thresholdRange: { min: 99 }
interval: 1m
- name: request-duration
thresholdRange: { max: 500 }
interval: 30s
Flagger 会自动创建 VirtualService 并根据指标推进流量迁移。
流量镜像(Shadow Traffic)
流量镜像可将生产流量副本发送到新版本服务,便于在不影响用户的情况下验证新代码。
- 配置 VirtualService 镜像流量:
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: catalog
spec:
hosts: [ catalog ]
gateways: [ mesh ]
http:
- route:
- destination: { host: catalog, subset: version-v1 }
weight: 100
mirror:
host: catalog
subset: version-v2
集群外流量管理与 ServiceEntry
Istio 默认允许出站流量。为提升安全性,可设置 outboundTrafficPolicy.mode=REGISTRY_ONLY,仅允许注册表白名单服务访问外部。
- 配置 ServiceEntry 允许访问外部服务:
apiVersion: networking.istio.io/v1alpha3
kind: ServiceEntry
metadata:
name: jsonplaceholder
spec:
hosts: [ jsonplaceholder.typicode.com ]
ports:
- number: 80
name: http
protocol: HTTP
resolution: DNS
location: MESH_EXTERNAL
总结
- Istio 通过 VirtualService 和 DestinationRule 实现细粒度流量路由,支持暗启动、金丝雀、镜像等多种发布策略。
- Flagger 可自动化流量迁移,降低人工操作风险。
- ServiceEntry 结合出站策略提升集群安全性,精细控制外部访问。
- 合理利用流量治理能力,有效降低新版本发布风险,提升微服务系统的可用性与安全性。