This article uses my personal experience with the “GitHub × Gitcoin Developer Fund 2025” phishing incident to systematically break down the profit chain, attack process, technical implementation, and defense strategies, helping the tech community identify and respond to new Web3 scams.
Introduction
Recently, I received an email on GitHub disguised as a “GitHub × Gitcoin Developer Fund 2025” notification, claiming I was “eligible” and only needed to click a link, verify my wallet via Gitcoin Passport, and pay a “refundable deposit” to receive funding. Many developers have reported similar emails; see Community Discussion #174283.
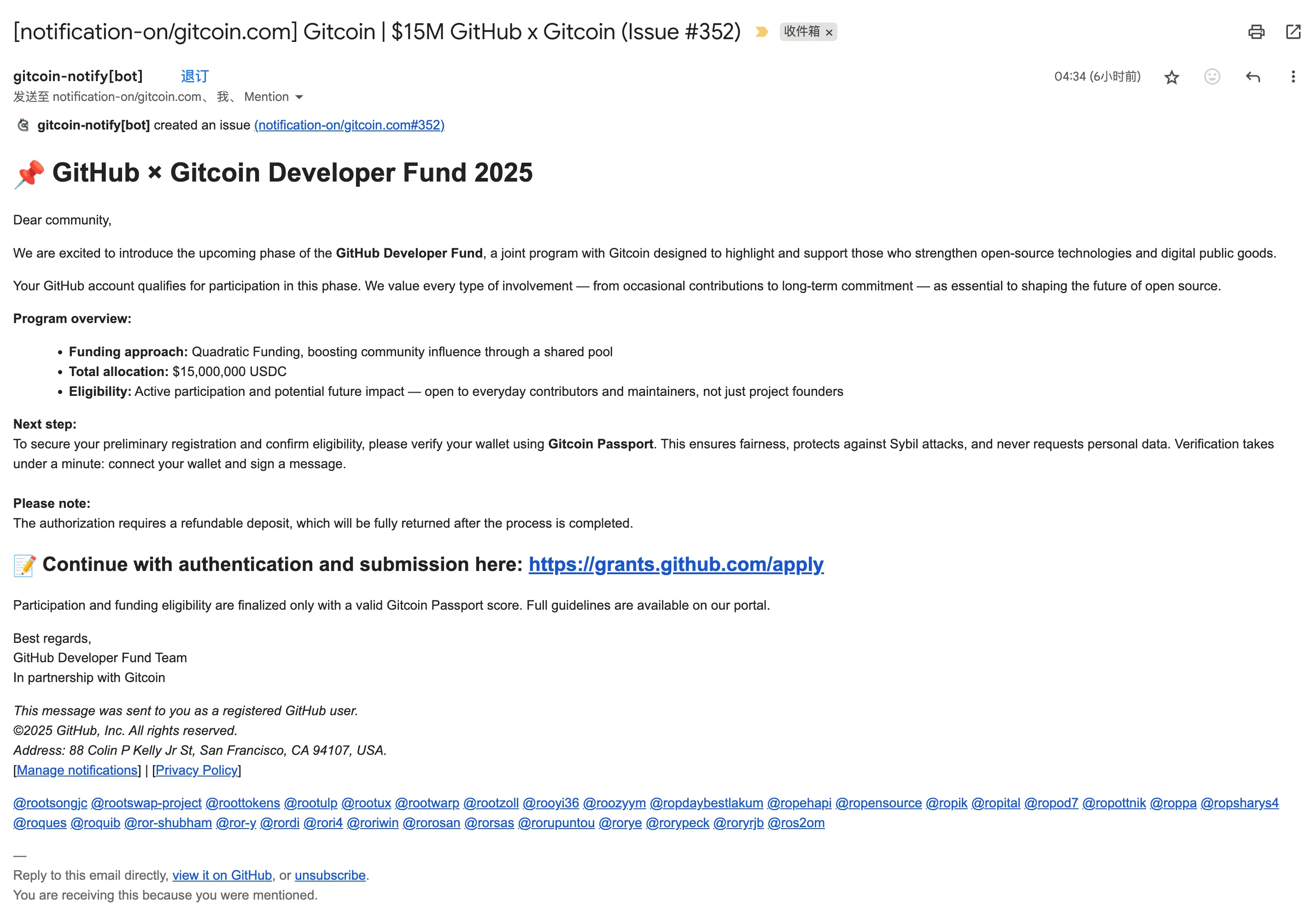
This scam exploits the authority of GitHub’s notification system, combines Web3 wallet authorization and deposits, and masquerades as a prestigious funding program—while in reality, it’s a scheme to steal funds and accounts. This article analyzes the profit motives, attack chain, technical details, and defense measures.
GitHub Notification “Shell” and Phishing Entry Point
Attackers use scripted accounts to create Issues or Discussions in unfamiliar repositories and @-mention thousands of developers (including myself), triggering GitHub’s system notification emails. This easily bypasses spam filters and lands directly in inboxes. Even experienced developers may let their guard down due to the “official GitHub notification” format.
Example link: Phishing Issue (GitHub Issue, safe to click)
Phishing Page Analysis and Typical Features
Visiting the phishing site github-foundation.com, any click on the page triggers a “Connect Wallet” popup, supporting MetaMask, Trust Wallet, WalletConnect, and other mainstream wallets.
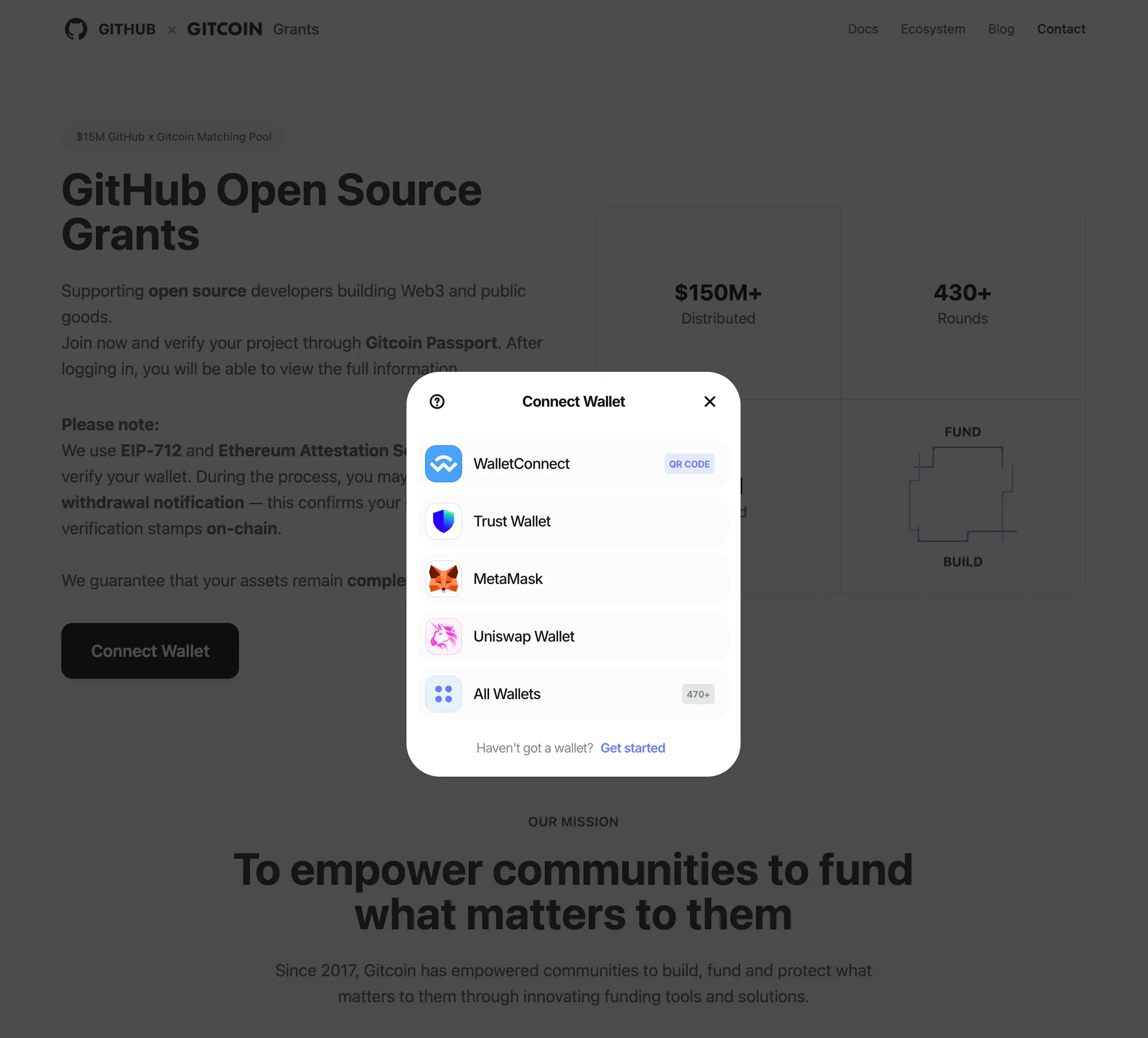
Key features include:
- Domain Spoofing:
github-foundation.comis completely different from the official domain. - Full-screen Inducement: The page contains no real information; all actions lead to wallet connection.
- Fake Endorsements: Displays real Gitcoin data but out of context.
- Wallet Trap: After authorization or deposit, funds and permissions are stolen.
Target Profile and Attack Strategy
Attackers prioritize developer accounts with influence and assets, such as GitHub Developer Program members, those with Sponsors, or high activity. These accounts are more likely to click the link and have higher-value wallets and repository permissions.
At the same time, attackers use a wide-net strategy, mixing high- and low-value users. Even a few victims yield profit.
Profit Chain and Attack Process
The complete profit chain is as follows:
- Traffic Acquisition: Mass account posting, @-mentioning users, leveraging GitHub email notifications.
- Conversion Design: Fake domains, copy, and partners to create an “official” feel.
- Profit Methods: Deposit payments, unlimited wallet authorization to steal assets, GitHub authorization for supply chain attacks.
- Risk Hedging: Disposable accounts, mass deployment, quick exit.

Technical Implementation and Engineering Details
- Exploits GitHub notification system to increase delivery success.
- Typosquatting domains mimicking github.com.
- Social engineering via wallet interaction, using “just signature, no charge” to lower defenses.
- Mass @-mentions for wide coverage and low attack cost.
- Subsequent GitHub authorization may inject malicious code.
Community Feedback and Victim Reports
In the GitHub Community discussion area, developers have reported similar spam, indicating the scam is spreading widely and is not an isolated case.
How to Delete the Spam Notifications
For cleaning up spam or “phantom” notifications caused by this type of phishing, refer to the effective solution in the community discussion. Download the cleanup script below and run it locally with node remove_phantom_notifications.js TIMESTAMP:
| |
For example, to clean phantom notifications after September 25, 2025:
node remove_phantom_notifications.js 2025-09-25T00:00:00Z
Defense and Emergency Measures
Here are some defense strategies:
- Personal Defense:
- Treat any wallet signature or deposit request as suspicious; assume a scam by default.
- Enable GitHub 2FA and regularly audit OAuth Apps, PATs, SSH Keys; revoke anything suspicious.
- Use email filters to auto-label notifications with keywords like
Gitcoin,Fund,Passport, orUSDC.
- Organization Defense:
- Enforce SSO and least privilege access.
- Restrict external app authorizations and unify official funding entry points.
- Prepare rapid emergency plans for key revocation and repository isolation.
- Post-Incident Actions:
- Revoke wallet authorizations.
- Delete suspicious GitHub authorizations, tokens, and SSH keys.
- Audit repository secrets and GitHub Actions.
- Report phishing domains, accounts, and repositories.
IOC Appendix (Indicators of Compromise)
- Phishing Domain:
github-foundation.com - Common Keywords:
GitHub × Gitcoin Developer Fund 2025,refundable deposit,Gitcoin Passport verification - GitHub Behavior: Mass unfamiliar accounts posting Issues/Discussions, @-mentioning hundreds of unrelated developers.
Summary
This case reveals a new type of phishing scam at the intersection of open source and Web3. Attackers exploit GitHub’s notification mechanism, combine wallet authorization and deposit monetization, and leverage large-scale engineering and platform endorsement. Effective defense requires zero trust for funds and authorizations, always using official entry points, and both individuals and organizations should implement least privilege principles and raise security awareness.
