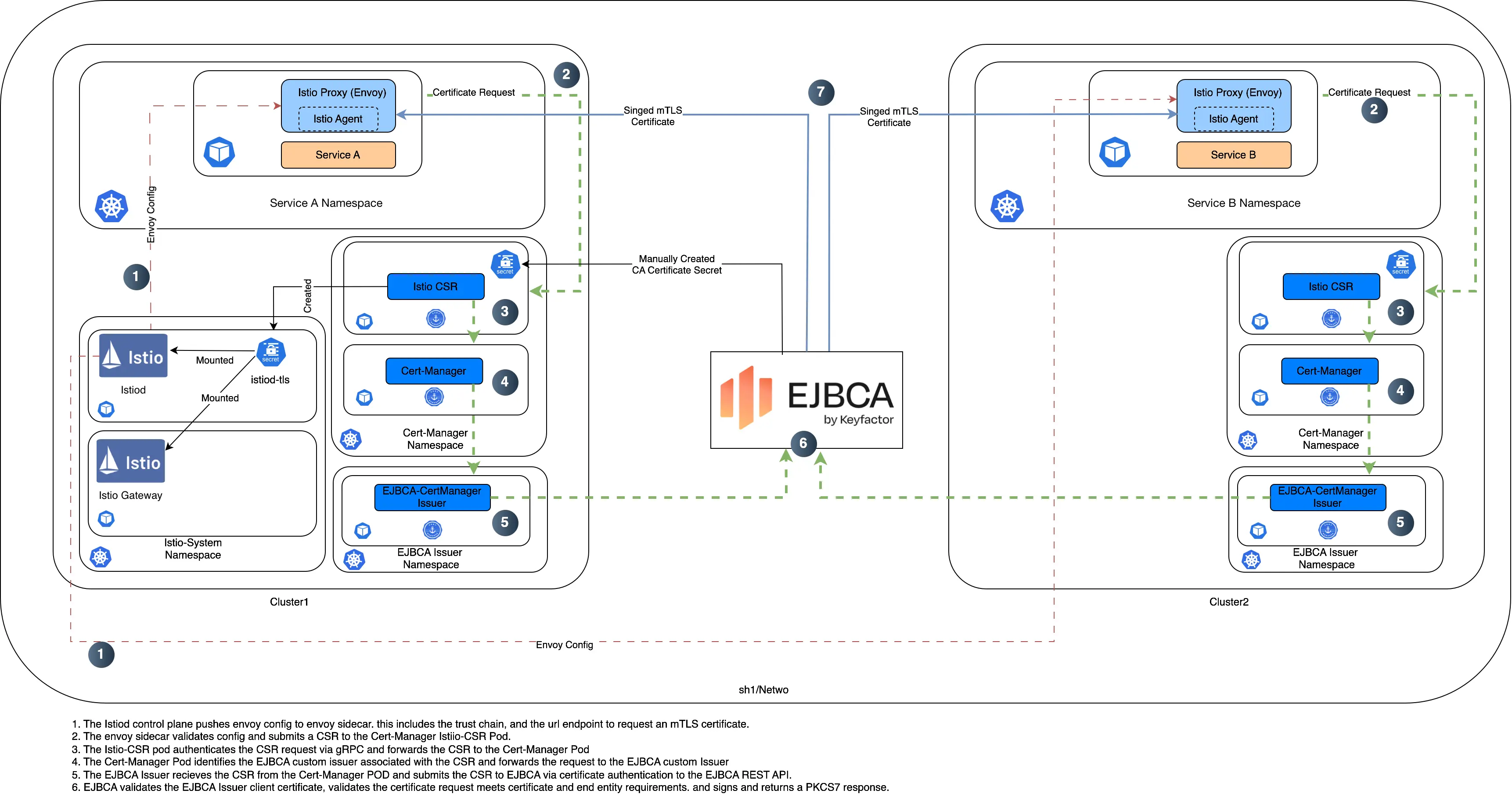
This article focuses on implementing PKI for Istio in a multi-cluster environment. It details the combination of EJBCA and cert-manager, including setup steps and emphasizes the importance of PKI best practices for secure and compliant service mesh.
Istio Column
Istio service mesh technology and practical tips.
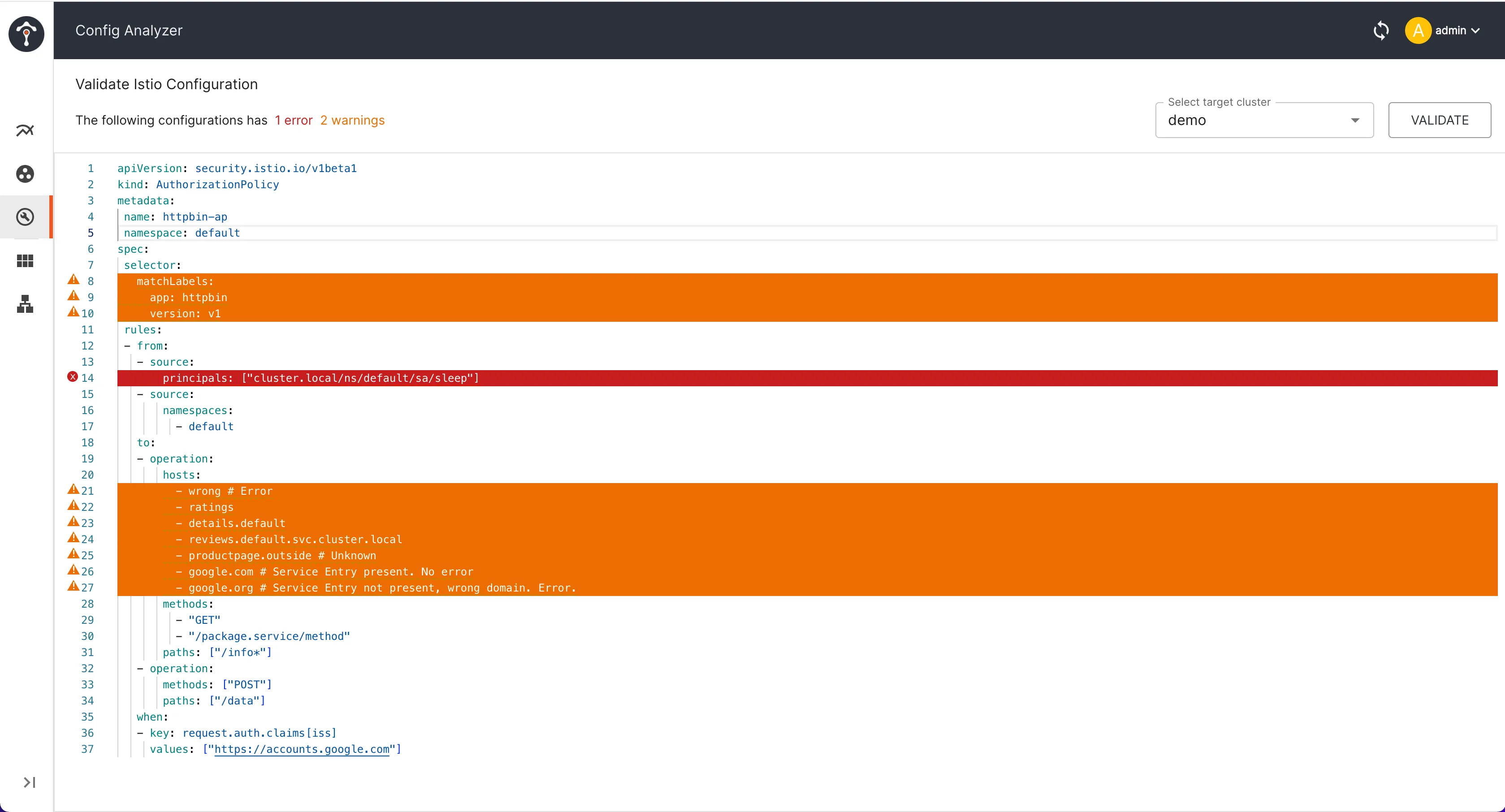
Istio Configuration Security: How to Avoid Misconfigurations
Explore common Istio configuration errors and their solutions to enhance the security and stability of your service mesh.
Securing Istio: Addressing Critical Security Gaps and Best Practices
Exploring security gaps in Istio and effective mitigation strategies, combined with best practices for multi-layered security.
A Definitive Guide to Cross-Cluster Seamless Access in Multicluster Istio Service Mesh
Explore how to effectively implement cross-cluster seamless access in the Istio multicluster mesh using SPIRE federation, DNS proxy, and east-west gateway technologies. This guide provides detailed configuration examples and steps to help you overcome deployment challenges and ensure efficient, secure communication between services.
How to Integrating Third-Party Service Registries with Istio?
This article provides a detailed introduction on how to integrate third-party service discovery mechanisms such as Consul and Eureka with Istio, achieving seamless service discovery integration.
Deep Dive into Istio 1.22: New Features and Practical Application Advice
Explore the new features and practical advice of Istio 1.22, including the delta xDS, path template support, and API upgrades, to optimize service mesh management.
Istio CNI Unveiled: Streamlining Service Mesh Connectivity
This article provides a detailed explanation of the design principles, implementation methods, and how to enhance security and permission management through Ambient Mode in the Istio CNI plugin.
Analysis of the Limitations of Istio Ambient Mode
In-depth discussion on the Ambient mode in Istio 1.22, comparison with the traditional Sidecar mode, and its limitations.
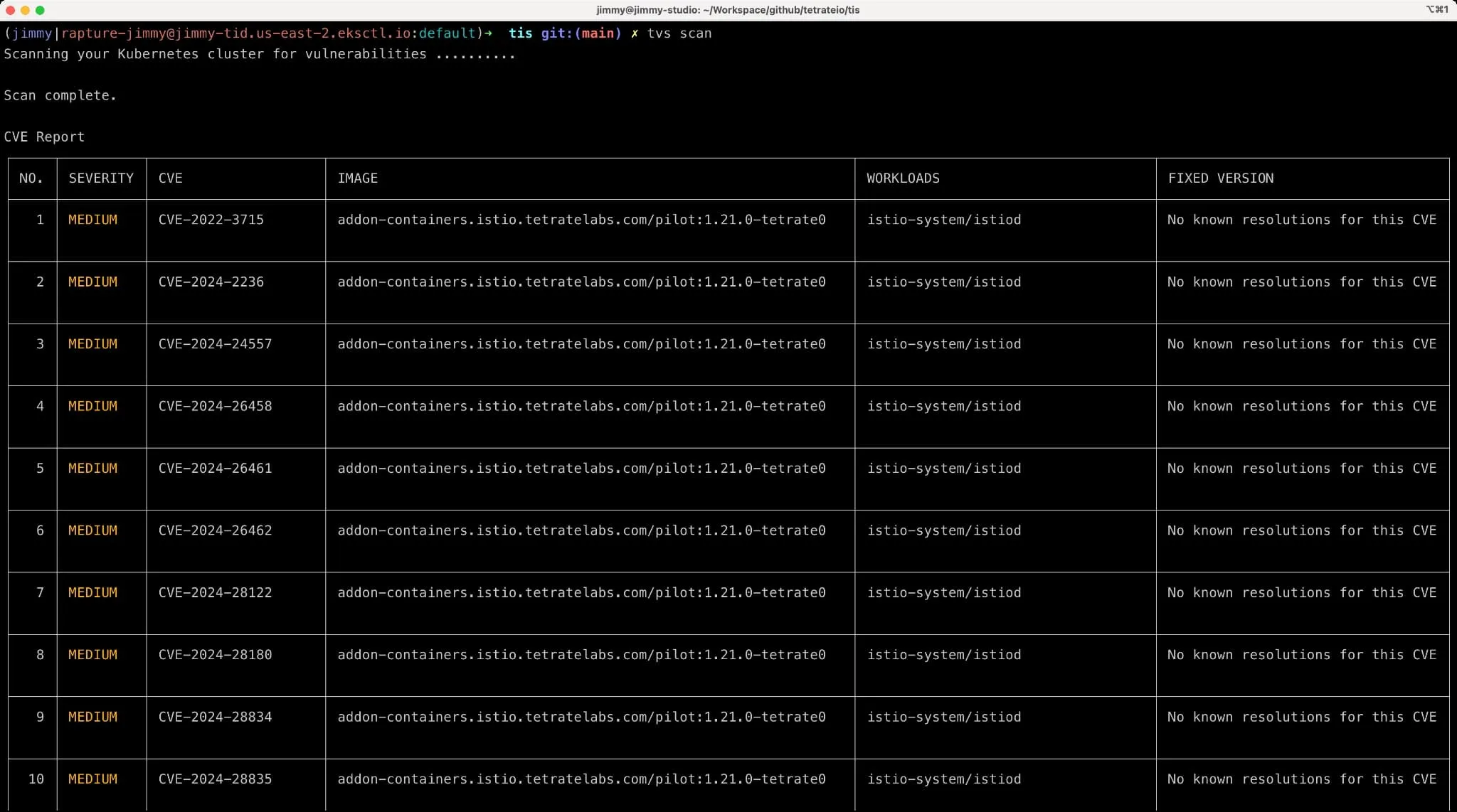
TVS: Istio and Envoy CVE Scanning Solution
This article will introduce Tetrate’s newly launched tool – Tetrate Vulnerability Scanner (TVS), a CVE scanner customized for Istio and Envoy.